How Identity Verification Prevents Rental Fraud
Use document checks, biometrics, and database validation to stop synthetic and stolen identity fraud in rentals and reduce costly evictions, losses, and reputational harm.
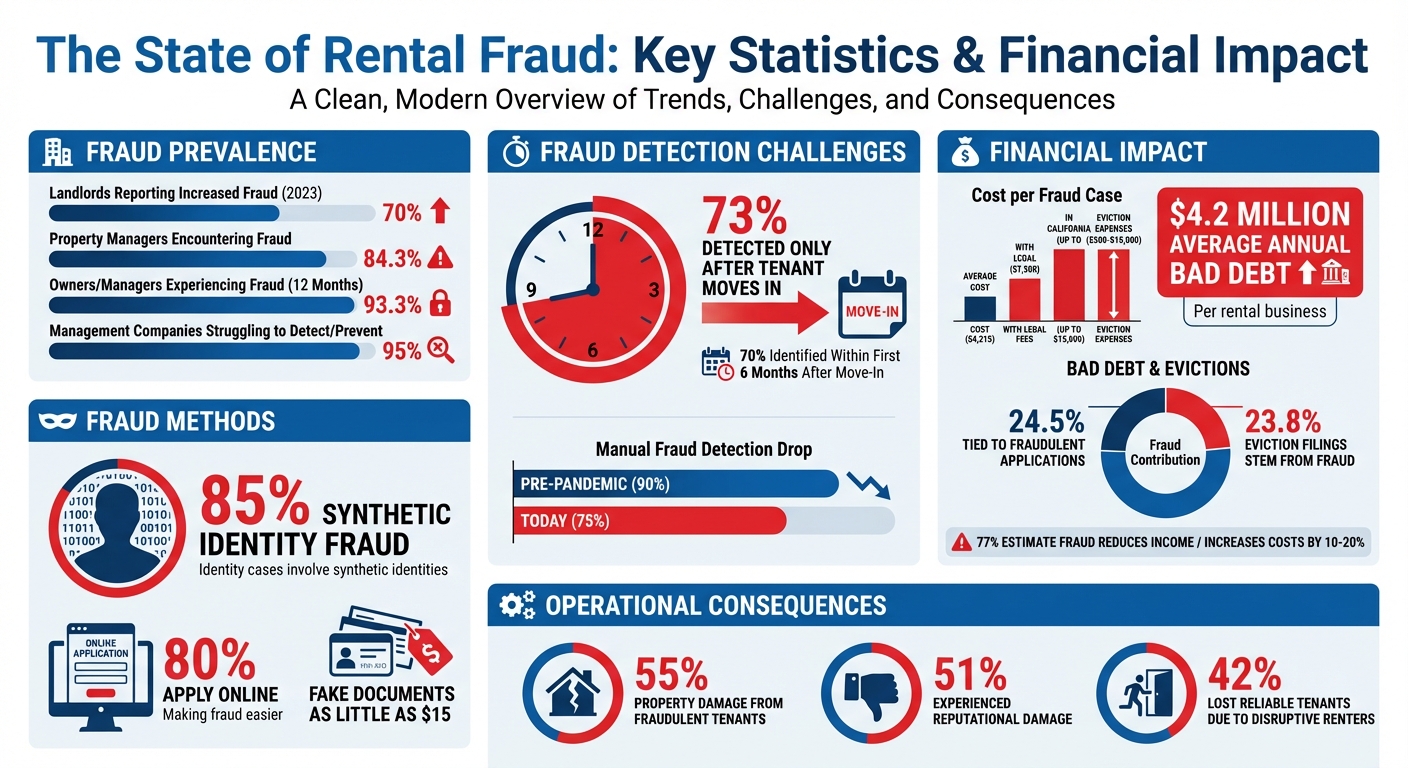
Rental fraud is a growing problem, costing U.S. businesses billions annually. Fraudsters exploit weak verification processes, using fake or stolen identities to secure rentals they don’t qualify for. In 2023, over 70% of landlords reported increased fraud, with 84.3% of property managers encountering fraudulent applications. This issue drives up costs, with eviction expenses ranging from $500 to $15,000 and lost income averaging $4.2 million per year for rental businesses.
Key Takeaways:
- Fraud methods include synthetic identities, stolen information, and fake documents.
- 85% of identity fraud cases involve synthetic identities.
- Modern tools like AI make creating fake pay stubs or IDs fast and cheap.
- 73% of fraud cases are detected only after tenants move in.
Solution: Automated identity verification helps stop fraud before it starts. By combining document checks, biometric matching, and database validation, rental businesses can catch fake applications early, avoiding costly evictions and reputation damage. Platforms like Lockii integrate these tools into a seamless, contactless rental process, ensuring only legitimate tenants are approved.
Rental Fraud Statistics and Financial Impact on Property Managers
Identity Fraud is on the Rise | Ashley Hawks | Black & Cherry Real Estate | Property Management
What Is Rental Fraud and How Does It Happen?
Rental fraud happens when scammers use false or stolen information to secure a property they wouldn’t otherwise qualify for. Over time, their methods have become more advanced, making it harder for rental businesses to catch fraudulent applications before it’s too late.
Common Fraud Methods
One of the most concerning methods is synthetic identity fraud, which makes up an estimated 85% of all identity fraud cases in the U.S.. In this scheme, fraudsters combine stolen data - like Social Security numbers from children or elderly individuals - with fake names and birthdates to create entirely new credit profiles that appear legitimate to screening systems.
Another tactic is third-party fraud, also known as traditional identity theft. This involves using someone else’s personal information, such as their name, Social Security number, and date of birth, to apply for rentals. Meanwhile, identity-manipulation fraud takes a slightly different approach: applicants tweak their own information - like altering a few digits in their Social Security number or misspelling their name - to avoid detection of negative credit history during background checks.
With modern technology, income and document fraud has become alarmingly easy to pull off. Scammers can use software or AI tools to generate fake paycheck stubs, W-2 forms, or bank statements in just minutes, often for as little as $15. Some even purchase Credit Profile Numbers (CPNs) online to replace Social Security numbers, allowing them to bypass credit checks and create what looks like a clean credit history.
Another form of fraud, first-person fraud, occurs when someone uses their real identity but has dishonest intentions - like subletting the property without permission or turning it into an unauthorized Airbnb. The rise of online rental applications has made this easier, as fraudsters can submit forged documents without ever meeting property managers face-to-face.
"Up to 80 percent of applicants apply online, and that makes it easier to pose as someone else. You can't verify their identity." - Mark Wilkinson, RealPage Screening
These advanced schemes create serious financial and operational headaches for rental businesses.
How Fraud Affects Rental Businesses
The growing complexity of fraud has made effective identity verification more critical than ever. The financial toll is staggering: 93.3% of apartment owners, developers, and managers reported experiencing fraud within a 12-month period. On average, a single case of fraud costs around $4,215, but that number can climb to $7,500 with legal fees and even reach $15,000 in states like California, where strict eviction laws drive up costs.
Rental businesses reported writing off an average of $4.2 million in bad debt over a year, with 24.5% of that debt tied to fraudulent applications. Additionally, 23.8% of eviction filings stem from these fraudulent cases.
The operational challenges go beyond financial losses. 73% of fraud cases are only discovered after the tenant has moved in, leaving businesses to deal with lengthy and expensive eviction processes while losing rental income. 55% of property managers also reported property damage caused by fraudulent tenants, adding repair costs to the list of expenses.
Fraud doesn’t just hurt the bottom line - it can also tarnish a business’s reputation. 51% of operators reported reputational damage due to fraudulent activity, and 42% said they lost reliable tenants because of the disruptive behavior of fraudulent renters. When bad tenants engage in criminal or disruptive actions, it drives away quality residents and harms the property’s standing in the market.
"73% of owner/managers identify fraud after the applicant moves in and over 70% identified the fraud within the first six months after move-in, leading to forced turnover well before the typical end-of-lease cycle." - National Apartment Association
Adding to the problem, 95% of property management companies struggle to detect or prevent fraud, and 77% of multifamily professionals estimate that fraud reduces income or increases costs by 10% to 20%. These statistics highlight how rental businesses are struggling to keep up with increasingly advanced fraud tactics.
How Identity Verification Stops Rental Fraud
Identity verification acts as a powerful shield against rental fraud by introducing multiple layers of protection. With manual fraud detection rates dropping from 90% pre-pandemic to just 75% today, modern verification systems have stepped in to fill the gap.
The magic lies in combining three key methods: document verification, biometric verification, and database validation. Each tackles a specific vulnerability that fraudsters often exploit. Document verification spots forged or altered IDs, biometric checks ensure the applicant is physically present and matches their ID, and database validation confirms the identity exists in official records. Together, these methods create a strong defense against even the most complex fraud tactics, like synthetic identities.
Document Verification
Document verification uses automated tools to inspect government-issued IDs - like driver’s licenses and passports - for signs of forgery. These systems analyze intricate security features such as barcodes, holograms, watermarks, and font consistency. Fraudsters often miss these details when creating fake documents.
The technology digs deeper, examining metadata and checking for signs of digital tampering. It can detect inconsistent fonts, blurry images, or any subtle irregularities that might signal a falsified document. This matters because today’s AI tools can churn out convincing fake IDs in just minutes.
"If a prospective tenant lies about who they are, the rest of their application is moot." - Briana Ings, Chief Product Officer, Snappt
Typically, applicants are required to upload high-resolution scans of original documents rather than photocopies, which can obscure signs of forgery. The system then compares these documents against official templates, flagging anything that deviates from the standard.
Biometric Verification
While document verification ensures the ID is legitimate, biometric verification confirms the person behind it is real. Applicants are asked to provide a live selfie or video, which is then matched against their submitted ID.
Liveness detection adds another layer of security by ensuring the person is physically present during the process. It can identify attempts to use printed photos, masks, or even deepfake videos. To verify liveness, the system might ask the applicant to perform simple actions like blinking, smiling, or turning their head. This step is particularly crucial for contactless rental operations, where in-person meetings are rare.
Database Validation
Database validation cross-references the applicant’s information - like name, Social Security number, date of birth, and address - against trusted records from credit bureaus, utility companies, and government databases. This step is key to detecting synthetic identity fraud, where fraudsters blend real and fake details to construct a convincing identity.
For example, the system can verify if a Social Security number is tied to a different name, belongs to a deceased person, or if the provided address matches utility or property records. It also prevents issues like “mixed reports,” where credit data from two individuals with similar names gets mistakenly merged. Without database validation, a fraudulent applicant could present a seemingly valid credit score or employment history, but deeper checks might reveal mismatched details - like a Social Security number issued to a minor or conflicting personal information.
Rental platforms like Lockii integrate these advanced verification methods to secure contactless rental processes, ensuring only legitimate tenants make it through the system.
sbb-itb-eb44693
How to Implement Identity Verification in Your Rental Business
Setting up identity verification for your rental business isn't just about meeting legal standards - it's also a powerful way to protect against fraud and ensure smooth operations. To get started, you'll need a clear and efficient workflow that determines when and how you'll collect identity information.
Building Verification Workflows
An effective identity verification process typically involves four steps: document collection, automated inspection, biometric matching, and data validation. Start by collecting government-issued IDs through a secure online portal instead of email to protect sensitive information. Automated tools can then analyze these documents for security features, flagging any signs of tampering.
Next, require applicants to take a live selfie, which can be matched to their ID photo using liveness detection technology. Finally, cross-check the applicant's name, Social Security number, and date of birth against trusted databases to confirm their identity.
Take the example of Padsplit, a co-living marketplace. In December 2024, they adopted Plaid’s automated identity and income verification tools. By replacing manual reviews with instant bank-link verification, they reduced their manual workload by 70% and cut application processing times to under 60 seconds.
It’s also important to differentiate identity proofing, which happens during the initial application process, from ongoing verification for activities like logins, payments, or maintenance requests. For a fully contactless experience, consider adding multi-factor authentication (MFA) or PassKeys to prevent account takeovers after the initial rental stage.
Staying Compliant with Legal Requirements
Compliance is non-negotiable. The Fair Housing Act (FHA) mandates that you apply the same screening standards to all applicants. Asking different groups for different documents could be seen as discriminatory. Similarly, the Fair Credit Reporting Act (FCRA) requires written consent before running credit or background checks. If you deny an application based on a consumer report, you must provide an adverse action notice that includes the reporting agency’s details and informs the applicant of their right to dispute the information.
"A compliant policy only works if all employees follow it, so you'll want to hold regular staff meetings on topics like legal requirements and data security." – Noah Goldman, COO, Snappt
To ensure compliance, keep detailed and encrypted applicant records for at least 10 years, as recommended by the National Association of Realtors. Use systems with encrypted servers and multi-factor authentication to store sensitive tenant data securely. Look for identity verification tools that are SOC 2 certified and include compliance measures like KYC (Know Your Customer) and AML (Anti-Money Laundering) protocols in their workflows. If you're unsure about your processes, consult a legal expert to review your forms and workflows for adherence to local and state regulations.
Once you’ve covered the legal bases, you can shift your attention to using technology to simplify and enhance the rental experience.
Leveraging Technology for Contactless Rentals
Modern technology makes it easier than ever to offer contactless rentals. Platforms like Lockii automate identity verification and integrate it directly into the booking process. These tools allow renters to confirm their identity via their smartphone before they even arrive. Once verified, the system can release digital keys, enabling 24/7 self-service rentals.
"[Online identity verification technology] gives you such an advantage. There’s going to be a period of time where there are going to be a lot of stores that don’t change. You have to be the store in your market that does change and is able to better serve the needs of your tenants." – Dane Elefante, Chief Operating Officer, Platinum Storage Group
To reduce friction, choose web-based solutions that don’t require renters to download an app. This is especially useful for businesses operating across multiple locations or in tourist markets, as these tools often support a wide range of international documents, including visas and green cards.
Lockii’s platform, for example, integrates seamlessly with digital locks from IglooHome, payment processing through Stripe, and workflow automation tools like Zapier. This creates a fully contactless rental ecosystem that’s scalable without adding extra labor costs.
Conclusion
Identity verification plays a crucial role in shielding rental businesses from fraud, safeguarding finances, and fostering trust. With fraudulent rental applications on the rise, implementing automated verification is no longer optional - it's essential for staying ahead.
The stakes are high. Eviction proceedings alone can cost anywhere from $1,000 to over $5,000. Even more concerning, 73% of fraud cases are only uncovered after tenants have moved in. This makes a robust, multi-layered verification process critical to avoiding these expensive pitfalls.
Modern tools make this process easier and more efficient. Platforms like Lockii integrate identity verification directly into the booking process. Renters confirm their identity via smartphone, which then triggers the release of digital keys, enabling 24/7 contactless rentals. This not only reduces labor costs but also speeds up service and elevates the overall customer experience.
As the rental industry moves toward fully automated, contactless operations, businesses leveraging these technologies gain a significant advantage. Manual processes are increasingly unable to detect sophisticated fraud, making quick and reliable verification a necessity rather than a choice.
To stay competitive, establish a clear identity verification workflow, ensure compliance with legal standards like the Fair Housing Act and FCRA, and invest in scalable technology. By doing so, you'll protect your business and customers while preparing for the future of contactless rentals.
FAQs
How does identity verification help prevent rental fraud?
Identity verification plays a key role in stopping rental fraud by ensuring applicants are who they claim to be. It helps catch attempts to use fake identities, stolen personal details, or forged documents during the rental process. By verifying IDs, such as driver’s licenses or passports, against reliable databases, rental businesses can confirm the legitimacy of applications and block fraudulent activity before it escalates.
This is particularly important for online or contactless rentals, where face-to-face checks aren’t an option. Automated identity verification tools simplify the process by flagging suspicious behavior, protecting your business from risks like unpaid fees or property damage, and preserving trust in your operations. These measures allow rental businesses to run with greater security and peace of mind.
How do scammers commit rental fraud, and what can be done to prevent it?
Scammers have a knack for finding ways to commit rental fraud, often by twisting the truth about who they are or their financial standing. A common trick? Submitting fake documents like doctored pay stubs or bogus employment records to make themselves look more qualified. Some take it a step further with identity theft, using stolen Social Security numbers or driver’s licenses to impersonate someone else. Then there’s the use of synthetic identities, where real and fake information are mixed to create entirely new, fraudulent profiles.
One of the best defenses against these scams is deploying identity verification tools. These tools are designed to spot inconsistencies, confirm personal details, and ensure applicants are who they claim to be. By tightening up verification processes, rental businesses can significantly lower the risk of fraud and keep their properties safe from scammers.
How does identity verification help rental businesses prevent fraud?
Identity verification plays a key role in helping rental businesses combat fraud and maintain secure transactions. By requiring customers to provide government-issued IDs, like driver’s licenses or passports, businesses can confirm the legitimacy of the individual. Advanced technology has made this process even more seamless, with tools that allow remote verification through smartphone scans or online uploads - perfect for contactless rental setups.
Pairing identity verification with features such as digital locks and automated systems, like those provided by Lockii, takes security to the next level. This combination not only cuts down on labor costs but also ensures that only verified individuals can access rentals. By integrating strong verification practices with automation, rental businesses can significantly reduce fraud risks while streamlining their operations.
